The primary work of mobile pentester is static and dynamic analysis of applications using some predefined tools like Jd-GUI or Frida and Objection. In this blog we will cover some concepts of dynamic analysis of android apps.
Dynamic analysis means interpreting or modifying the apps in runtime. In this blog we will cover the tool called Objection for Dynamic analysis of android app called diva-beta.apk and we will use Non-rooted android device POCO F1.
Link for the app will be provided below:-
What is Objection?
Objection is a tool using for Dynamic analysis of android based application. It allow us to assess mobile applications and their security posture without rooting and Jail breaking the mobile device. It is built on the top of the Frida which is also a great tool for dynamic analysis. Most of the Pentester Bug hunter using this tools now a days to perform Dynamic Application Analysis.
To start with Dynamic analysis of application, the first step in this process is to setup tool in your operating systems like Ubuntu, Kali Linux etc. we are going to cover all the steps to setup tool in Kali Linux, below are the steps for setting up the tool.
Step 1: Installation of Objection in Linux
We need to install Python3 and pip3, you can install the python and pip3 repo in Kali linux by using below syntaxes.
Sudo apt-get install python3 # it will install the python repo in you Kali
Sudo apt-get install pip3 # it will install the pip3 repo in your Kali
(Or) Sudo apt-get install python3-pip
After installing python and pip repo, the next step is to install Objection.
Note:-If you have Objection already installed then you can use pip3 install –upgrade objection for upgrading the version of Objection.
Pip3 install objection
Now we have to install some utilities for Objection. You just need run these commands.
Sudo apt install Zipalign
Sudo apt install aapt
Note: Zipalign is a tool for optimizing app and aapt turns your sdk resources in binary.
Step 2: Apktool installation:
Before going further, we can also setup Apktool, so below are steps available to setup process.
Download Linux wrapper script (Right click, Save Link As apktool)
https://raw.githubusercontent.com/iBotPeaches/Apktool/master/scripts/linux/apktool
Download apktool-2 (find newest here)
https://bitbucket.org/iBotPeaches/apktool/downloads/
After downloading the latest version, then rename downloaded jar to apktool.jar.
Next step is to move both files (apktool.jar & apktool) to location /usr/local/bin (root access required)
Make sure both files are executable if not then change the permissions using chmod (chmod +x).
Try running apktool via cli.
Step3: Installation of Jarsigner or Apksigner
Next step is to setup either Jarsigner or Apksigner in Kali linux. Why these tools are required.
The Jarsigner tool is used to sign Java Archive (JAR) files, and to verify the signatures and integrity of signed JAR files. The JAR feature enables the packaging of class files, images, sounds, and other digital data in a single file for faster and easier distribution. A tool named jar enables developers to produce JAR files. (Technically, any ZIP file can also be considered a JAR file, although when created by the jar command or processed by the Jarsigner command, JAR files also contain a META-INF/MANIFEST.MF file.)
To install Jarsigner below are the commands.
Sudo apt-get install Jarsigner or sudo apt-get install apksigner
What is patching and why do we require our apps to get patched?
Patching is a process through which, we are injecting Frida dylib library in our application which is apk file and install in our device i.e. POCO F1 (this device is using for this analysis).
Objection is built on top of Frida and objection is working on the basis of client-server model. So whenever we are patching applications we are injecting Frida dylib library into our app so that it will act as Frida server and our linux machine will act as client.
Commands for patching application.
In the terminal use below commands:
Objection –help
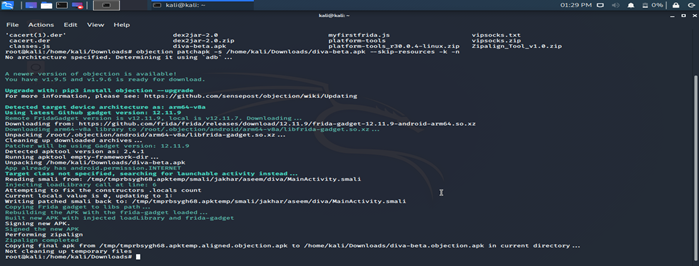
Objection patchapk -s /home/kali/Downloads/diva-beta.apk -a arm64-v8a
-s : stands for source
-a : stands for architecture
Note:-Objection will automatically detect architecture. In case if it is not detecting architecture we have to mention -a as mentioned. Objection is case sensitive.Dont use capital O so use small o.
Installation of patchapk
After patching a new file diva-beta.objection.apk is created in /home/kali/Downloads.
For installing patched apk “diva-beta.objection.apk” we have to run command:
adb install diva-beta.objection.apk
Note:-usb debugging should be enabled in your device for installing apps from adb. Usb debugging is in developed option. To enable developer option simply click on Build no or check device manual or search for your model no in any search engine.
For installation of adb here is link:
https://www.xda-developers.com/install-adb-windows-macos-linux/
Procedure after patching
Now the next step is to launch your patched diva beta.apk in our mobile device.

In this app we will try to trace hardcode part 1 classes and methods

Commencement of Objection in linux
For connecting our objection linux machine i.e. client to our server that is our mobile device POCO F1, we have to simply type the following command in you kali terminal for connecting client to server (patched apk).
objection explore
Hooking of classes and methods
For hooking classes and methods first we have to search the class and methods related to hardcode information. Here in app we will try to find it using we will try to find keyword called hardcode by using objection command Android hooking search class hardcode.
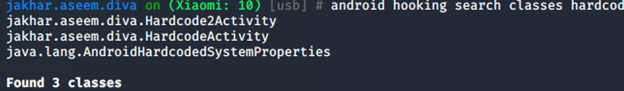
Now look at classes we found three classes. The class we will hook here is jakhar.aseem.diva.HardcodeActivity because it look familiar as per our need. Now we will watch for this method using Android hooking watch class jakhar.aseem.diva.HardcodeActivity
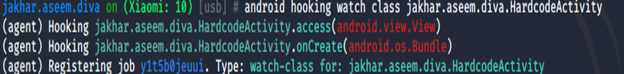
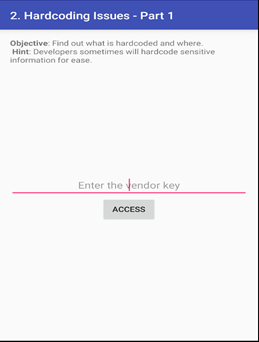
Now we found that whenever we click on access button we can find method of classes which are invoking at runtime. There are 3 methods invoking but one methods looks which we have some importance is jakhar.assem.diva.HardcodeActivity.access(android.view.view)
Now we found name of methods now we will try to hook these method using Android hooking watch class_methods jakhar.assem.diva.HardcodeActivity.access. You will get result like these
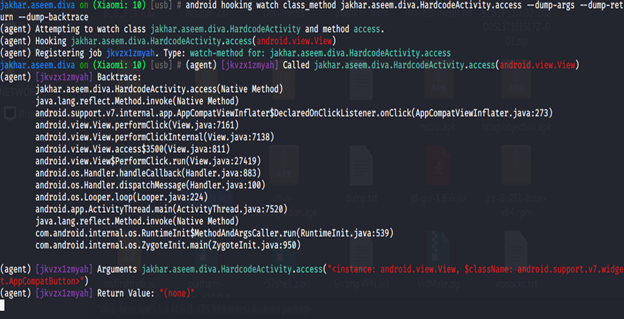
Note: we can use Android hooking watch classes Jakhar.aseem.diva.HardcodeActivity –dump-args –dump-return if you want return value and arguments.
Setting value using objection
We don’t have any method in diva-beta.apk but assume if we have is device rooted Boolean value in our class. Let us assume we have jakhar.assem.diva.usermainactivity class and jakhar.assem.diva.usermainactivity.is device rooted.
Now we want to try to set value to false using objection. Why this is required? Because sometimes apps are not running because of root functionality in phone, so what we can do here is to just bypass root detection for app by using objection. Android set return value jakhar.assem.diva.usermainactivity.is device rooted now false.
Final words
As we come to end of our journey assuming you like this blog. Objection is a great tool for dynamic analysis especially in case of when the code is obfuscated or not clear. Overall Objection is great tool for Dynamic analysis.
Troubleshoot
While performing the patching process, if you are facing trouble or getting error, so below is the error which you can get while doing this process. So to resolve issue you can do below steps.
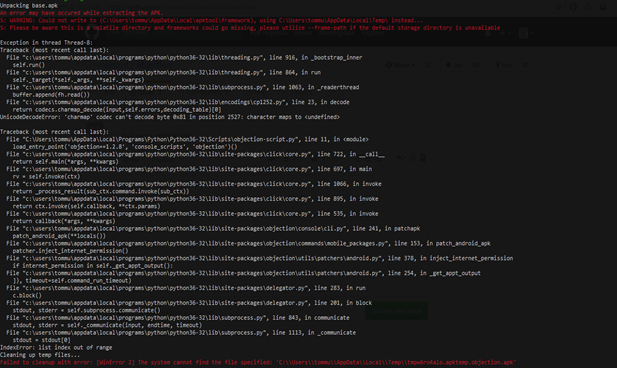
If your Objection is showing temporary file error then the command we have to run is:-
objection patchapk -s /home/kali/Downloads/diva-beta.apk –skip-resources -k -n
Note: in replace of –skip-resources we can use –D, -k stands for “not cleaning up temp files” and -n stands for ignore native libs